Scanning Options
Public Container Images
Scan any publicly available container image from popular registries:- Docker Hub: Pull and scan any public image directly by name
- Public Registries: Access images from GCR, ECR, and other public repositories
- Official Images: Scan official language runtime images, database images, and more
- Community Images: Analyze community-maintained containers for security issues
Private Container Images
Securely scan your organization’s private container images:- Private Registries: Connect to your private Docker registries with authentication
- Secure Access: Use API keys, tokens, or service accounts for secure access
- Organization Images: Scan custom-built images from your CI/CD pipelines
- Multi-Registry Support: Connect multiple private registries simultaneously
How Container Scanning Works
-
Image Selection
Choose to scan either a public image by name or connect to your private registry to select specific images. -
Layer Analysis
Our scanner analyzes each layer of your container image, examining:- Base operating system vulnerabilities
- Installed packages and libraries
- Application dependencies
- Configuration files
-
Vulnerability Detection
Identify security issues across multiple categories:- CVE Vulnerabilities: Known security vulnerabilities in packages
- Malware Detection: Scan for malicious code or suspicious files
- Secrets Scanning: Detect exposed API keys, passwords, or tokens
- Configuration Issues: Identify misconfigurations and security weaknesses
-
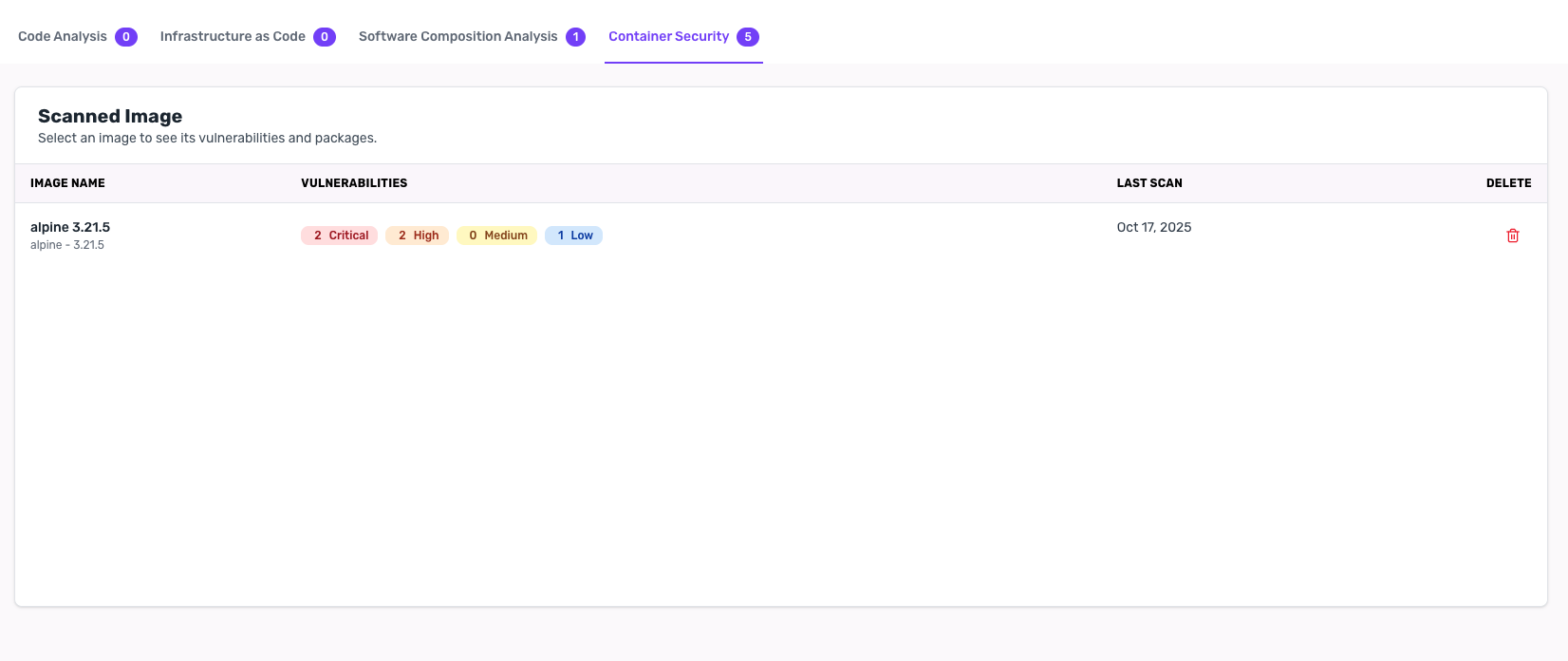
Results & Reporting
Get detailed reports with:- Vulnerability severity levels (Critical, High, Medium, Low)
- Affected packages and versions
- Remediation recommendations
- Layer-by-layer breakdown
Scanning Process
1
Select Image Source
Choose between public image scanning or connect to your private registry
2
Specify Image
Enter the image name and tag for public images, or browse your private registry
3
Configure Scan
Set scanning parameters and select vulnerability types to detect
4
Run Analysis
Our engine pulls and analyzes the container image layers
5
Review Results
Access comprehensive vulnerability reports and remediation guidance
Benefits
Early Detection
Identify vulnerabilities before deploying containers to production environments.
Layer Visibility
Understand which layer introduced specific vulnerabilities for targeted fixes.
Registry Integration
Seamlessly connect to multiple public and private container registries.
Compliance
Meet security compliance requirements for containerized applications.
Related: Dockerfile Scanning · Registry Integrations · Create a Project