What is a Security Champion?
In traditional organizations, a Security Champion is a designated expert—typically a senior developer with security expertise—who serves as the bridge between development teams and security departments.The Traditional Challenge
Human Security Champions face limitations:- Limited Availability: One person covering multiple teams
- Knowledge Bottlenecks: Development slows when unavailable
- Scaling Issues: Can’t maintain recommended 1:10 ratio as teams grow
- Timezone Gaps: Not available 24/7
The Cybe Solution
Cybe Security Champion gives every developer their own AI security expert:- 24/7 Availability: Always ready to help
- Instant Responses: No waiting in queue
- Unlimited Capacity: Serves all developers simultaneously
- Consistent Expertise: Same level of guidance for everyone
How It Works
Knowledge Graph Foundation
Cybe Security Champion leverages our proprietary knowledge graph created from your parsed codebase. This enables:- Full codebase understanding: Knows your architecture, dependencies, and patterns
- Context-aware responses: Answers specific to your code, not generic advice
- Accurate analysis: Zero hallucinations thanks to stored code context
Configuration
Requirements
Enable Cybe Security Champion
- Navigate to Project Settings
- Ensure Cybe Analysis is enabled
- Find the Cybe Security Champion section
- Toggle Enable Cybe Security Champion
- Save your settings
Once enabled, you can start chatting with your vulnerabilities and codebase immediately.
Using Cybe Security Champion
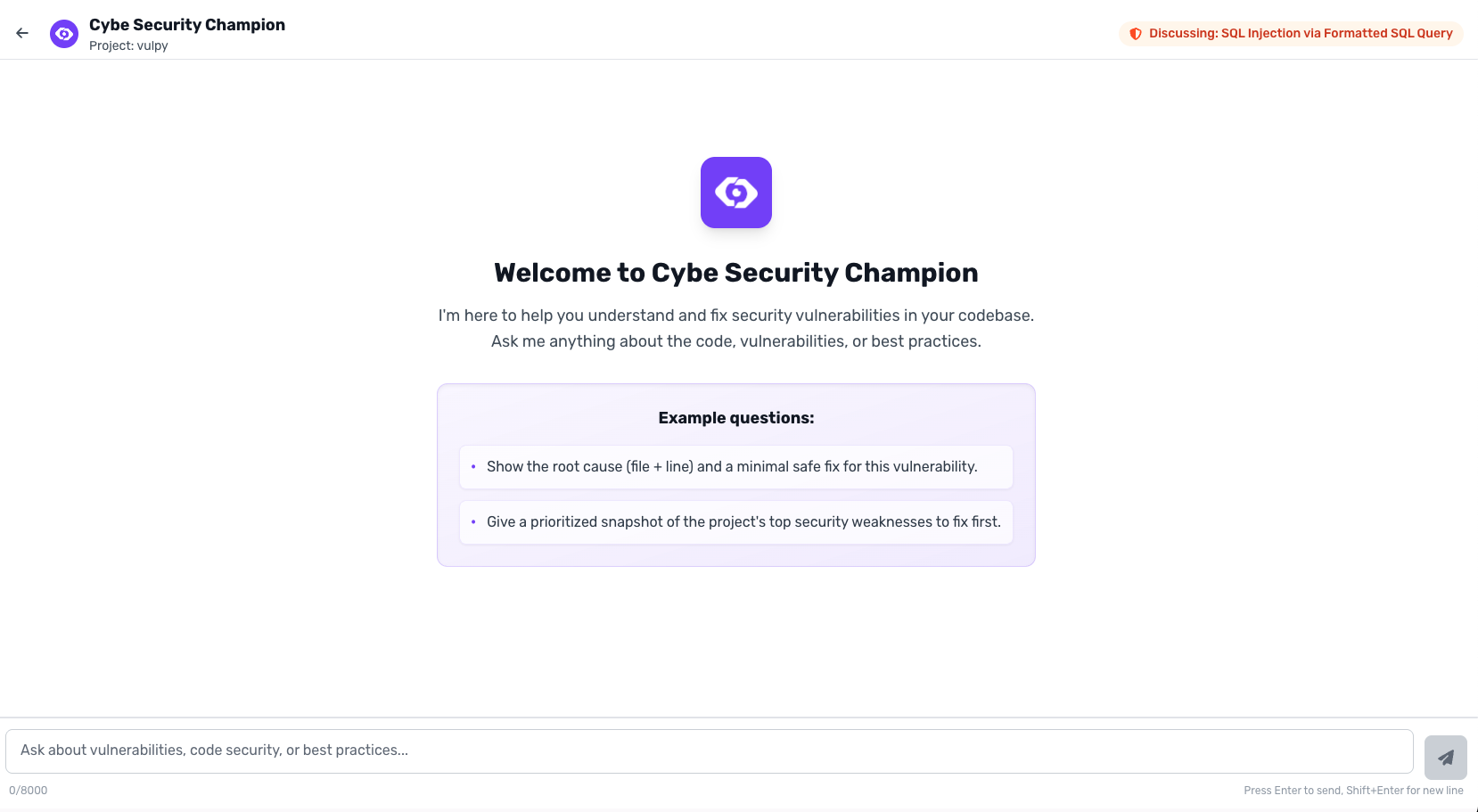
Chat with Vulnerabilities
Click the chat icon on any vulnerability to:- Ask about exploitation scenarios
- Understand the vulnerability’s context in your code
- Get remediation suggestions specific to your architecture
- Learn why this vulnerability exists and how to prevent it
- “How can this SQL injection be exploited in our application?”
- “What’s the business impact if this vulnerability is exploited?”
- “Show me the data flow that leads to this XSS issue”
Chat with Your Codebase
Open the general Cybe Security Champion chat to:- Ask questions about your application’s security posture
- Find specific security patterns in your code
- Understand how different components interact
- Get security recommendations for new features
- “Where are we validating user input in the authentication flow?”
- “Show me all database queries that use user-supplied data”
- “What security best practices should I follow for our payment module?”
What You Can Do
Interactive Security Consultation
Have natural language conversations about:- Specific vulnerabilities: Deep dive into findings
- Code patterns: Understand security implications
- Best practices: Learn secure coding for your stack
- Architecture decisions: Evaluate security trade-offs
Proactive Learning
Every interaction educates:- Why vulnerabilities occur: Understand root causes
- How to prevent them: Learn prevention techniques
- Security principles: Build security knowledge over time
Project-Specific Guidance
Unlike generic security advice, Cybe Security Champion provides insights tailored to:- Your application’s architecture
- Your technology stack
- Your specific dependencies
- Your business logic
Data Privacy
Read-Only Access
Cybe Security Champion has read-only access to your code through specialized tools. It cannot:- Modify your code
- Execute commands
- Access external systems
- Share data outside your region
Sovereign Storage
Your code is stored in your selected cloud region (EU or US) and:- Remains within your geographical boundary
- Complies with regional data regulations
- Is never used for model training
- Can be deleted when Cybe Security Champion is disabled
Limitations
When Cybe Security Champion is disabled:- Cannot chat with vulnerabilities
- Cannot chat with codebase
- Code is removed from storage
Requirements
- ✅ Cybe Analysis enabled (for code parsing)
- ✅ Project scanned at least once
- ✅ Code stored in sovereign cloud
- ✅ Sufficient Cybe Security Champion credits in your subscription
Related: Cybe Analysis · Cybe AutoFix · LLM Usage & Privacy · AI Usage Tracking