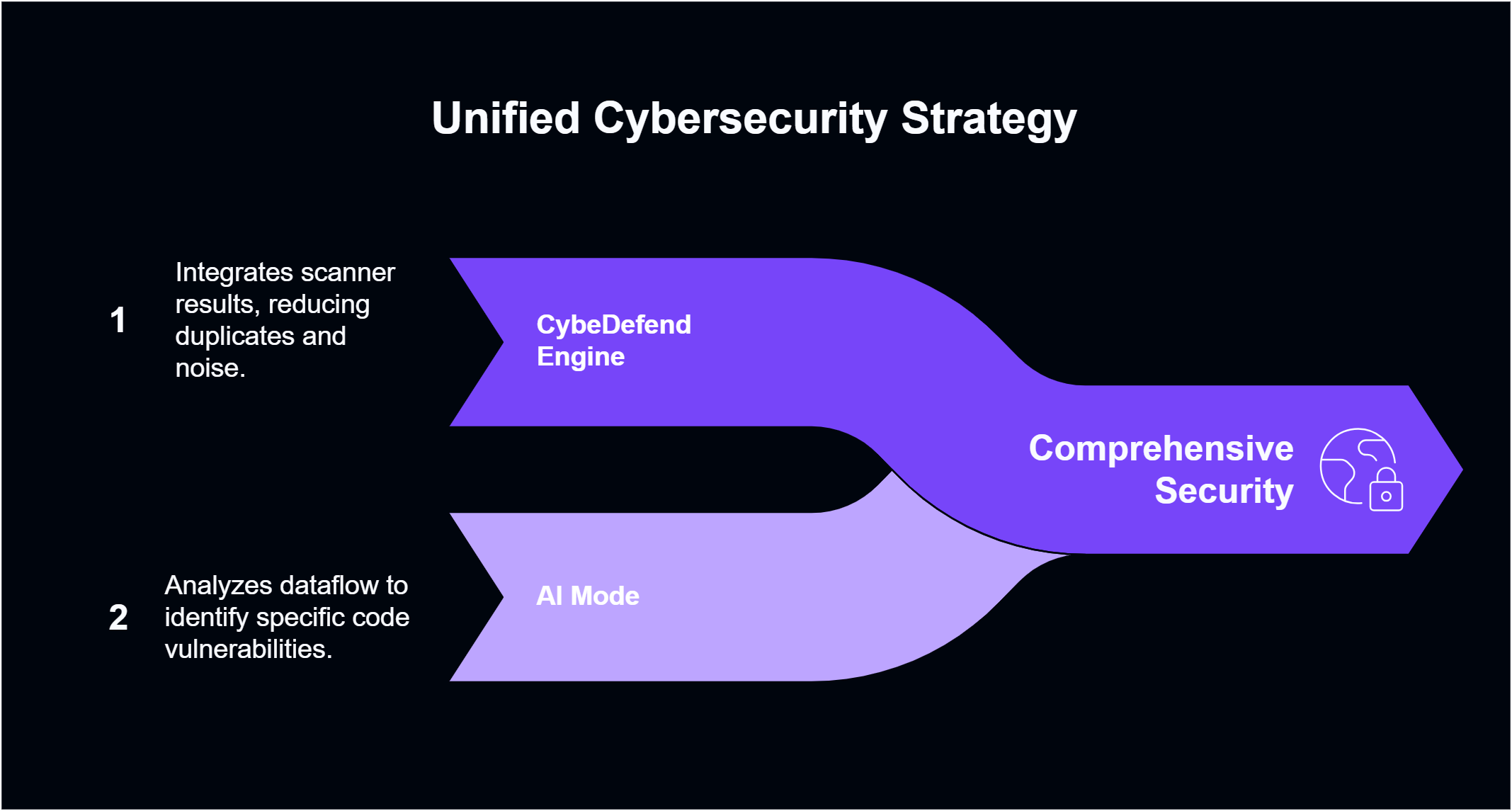
- CybeDefend Engine – Aggregates and cross-references results from multiple open-source and proprietary scanners, minimizing duplicates and noise.
- AI Mode (Optional) – Provides dataflow analysis in your code to distinguish static text issues from variable-based vulnerabilities, automatically building a flow of how data moves when a variable is implicated.
Why Use CybeDefend?
- Unified Scanning: The CybeDefend Engine merges findings from different tools into a single, concise view.
- Reduced Noise: Duplicate or overlapping vulnerabilities are identified and consolidated, preventing alert overload.
- AI-Driven Dataflow: If you enable AI Mode for your code scans, vulnerabilities referencing variables trigger automatic dataflow traces—highlighting truly exploitable paths in your application.
Want to see how to turn on AI Mode or watch a live code scan? Check our Scanning Demonstration.
1. Static Application Security Testing (SAST)
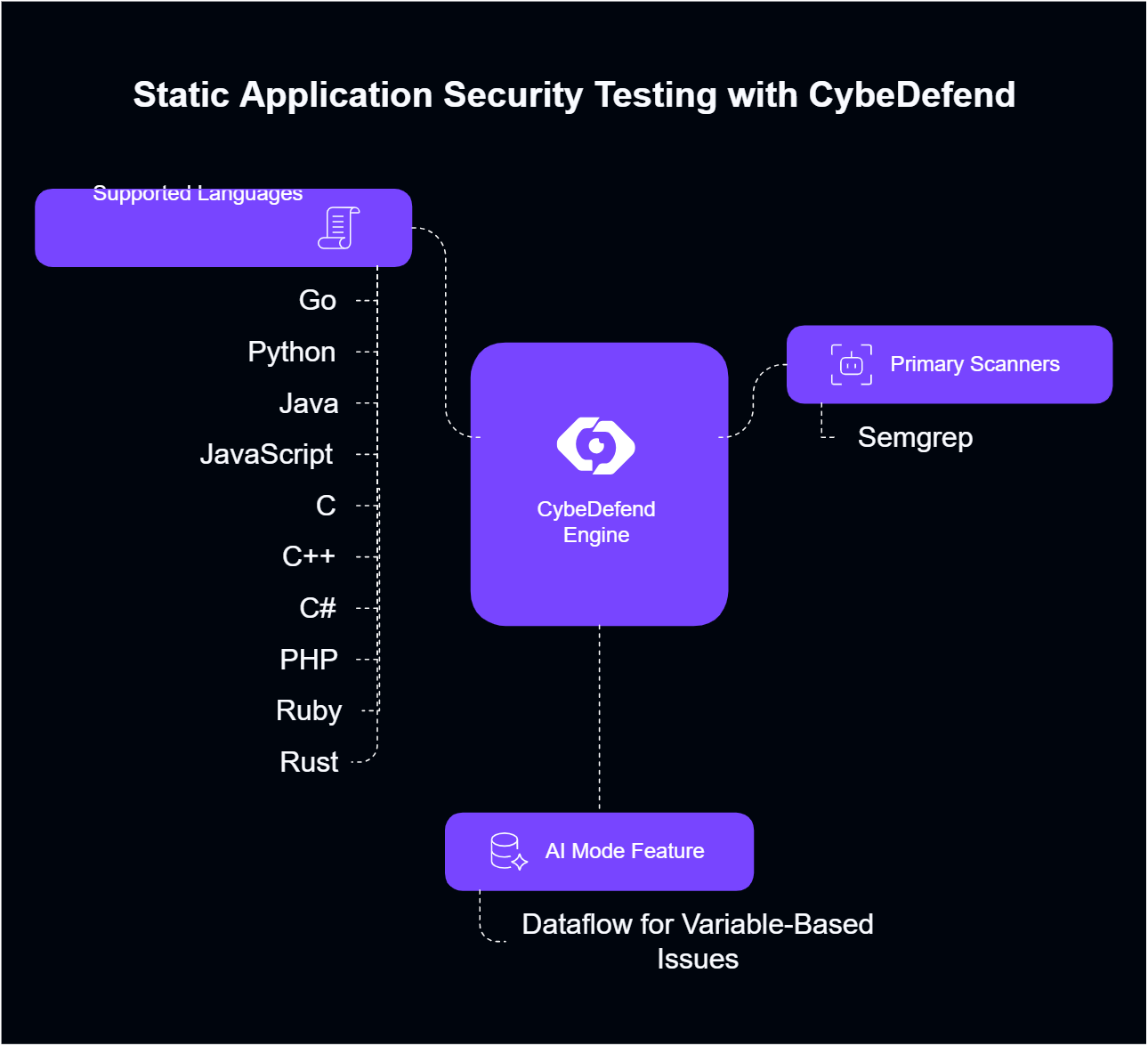
SAST inspects your source code to catch vulnerabilities early in the development process. CybeDefend unifies open-source scanners (e.g., Semgrep) under the CybeDefend Engine. If you enable AI Mode, we add line-level dataflow analysis—revealing when a flagged line involves a variable and automatically mapping its flow through your code.Supported Languages
| Language | Primary Scanners | AI Mode Feature |
|---|---|---|
| Go | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| Python | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| Java | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| JavaScript | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| C | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| C++ | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| C# | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| PHP | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| Ruby | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
| Rust | CybeDefend Engine + Semgrep | Dataflow for variable-based issues |
If the suspicious line references a constant, CybeDefend flags it accordingly. If it references a variable, the AI Mode can map that variable’s journey. See the Dataflow Analysis page for more details.
2. Infrastructure as Code (IAC) Security
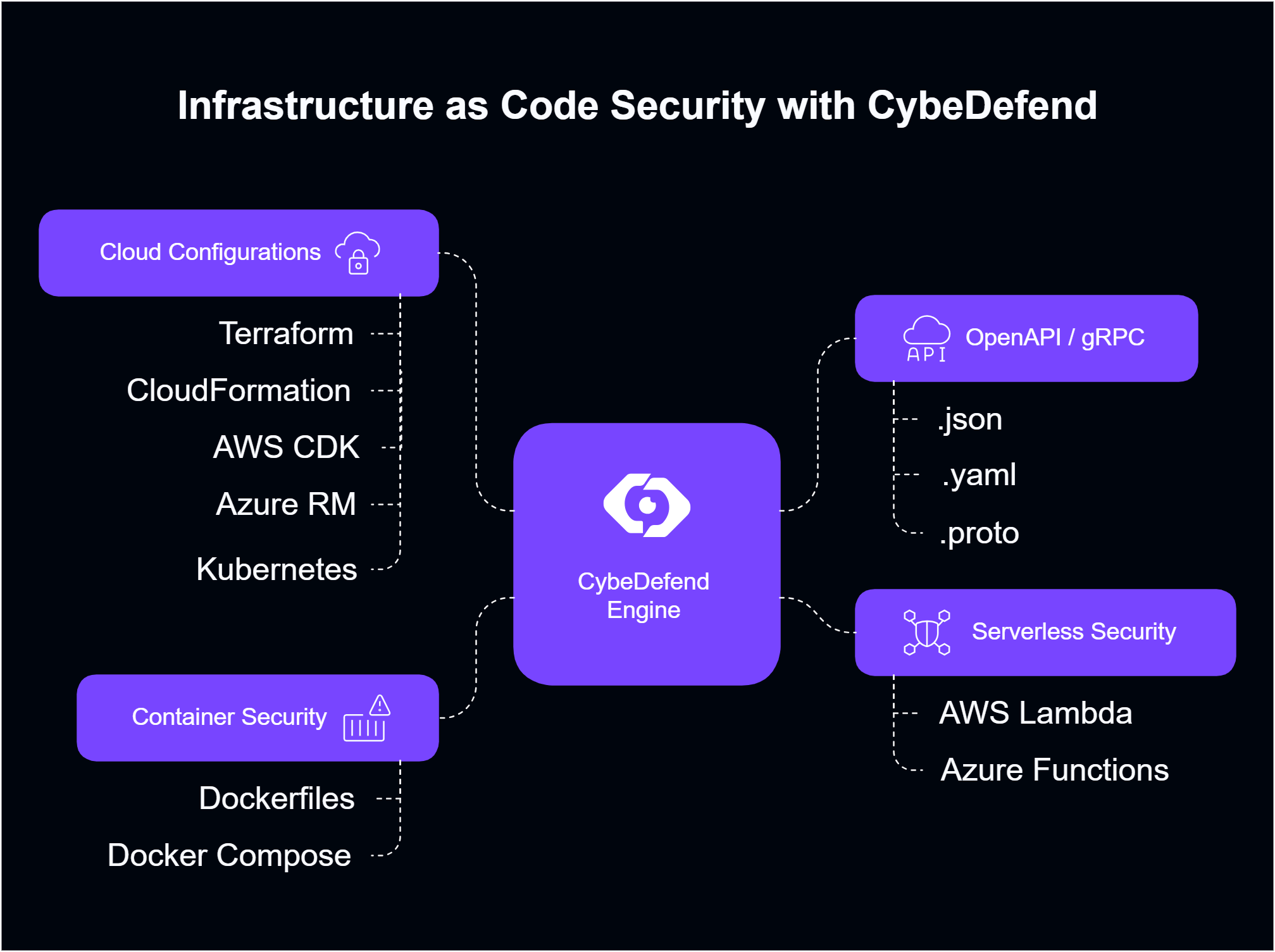
IAC scanning ensures that cloud and container configurations adhere to best practices. The CybeDefend Engine works with scanners like Checkov, Trivy, and KICS to identify misconfigurations. Unlike SAST, enabling AI Mode for IAC does not provide line-level dataflow (which is primarily for code), but the Engine still handles intelligent vulnerability matching and deduplication.Supported Technologies
| Category | IAC Types | Scanning Tools |
|---|---|---|
| Cloud Configurations | Terraform, CloudFormation, AWS CDK, Azure RM, Helm, Kubernetes | CybeDefend Engine + Checkov, KICS, Trivy |
| Serverless Security | AWS Lambda, Azure Functions | CybeDefend Engine + Checkov, KICS |
| Container Security | Dockerfiles, Docker Compose | CybeDefend Engine + Trivy, KICS |
| OpenAPI / gRPC | .json, .yaml, .proto | CybeDefend Engine + KICS |
IAC misconfigurations can lead to severe breaches. The CybeDefend Engine identifies issues in your code, saving you from manually piecing together results from multiple scanners.
3. Software Composition Analysis (SCA)
SCA detects vulnerabilities in third-party libraries and open-source dependencies. CybeDefend uses the CybeDefend Engine combined with GitHub Advisories to identify known flaws in your dependencies.SCA Scanning Tools
| Engine | External Advisory Source |
|---|---|
| CybeDefend Engine | GitHub Advisories |
Files & Package Managers
Below is a non-exhaustive list of key files we inspect:| Language/Framework | File Examples |
|---|---|
| Node | npm-shrinkwrap.json, yarn.lock, pnpm-lock.yaml, pnpm-lock.yml, bun.lock, bun.lockb, deno.lock, libman.json, package.json, package-lock.json |
| Java | gradle.lockfile, build.gradle, .jar, .war, .ear, pom.xml |
| Swift | Package.resolved, Podfile.lock |
| .NET (NuGet) | .deps.json, packages.lock.json, Packages.props |
| Kotlin | gradle.lockfile |
| Elixir | mix.lock |
| C/C++ | conan.lock |
| Scala | build.sbt, plugins.sbt, dependencies.scala, libraries.scala, .sbt.lock |
| Clojure | deps.edn |
| Generic | composer.json, requirements.txt, Pipfile, Pipfile.lock, poetry.lock, pyproject.toml, Gemfile, Gemfile.lock, Cargo.toml, Cargo.lock, go.mod, pubspec.yaml, pubspec.lock, packages.config, Package.swift, rebar.config, rebar3.config, rebar.lock, rebar3.lock, .gemspec, .csproj, .nuspec, .yml, .yaml |
If you use special file names or custom project layouts, you can configure file-patterns in the CybeDefend dashboard to ensure they are recognized and scanned.
Next Steps
Scanning Demonstration
Learn how to configure your scans, enable AI Mode for code analysis, and see real-time feedback on vulnerabilities.
Dataflow Analysis
Discover how AI Mode highlights true exploitability by mapping variable usage across your code.
Free Plan & Demo
Try CybeDefend at no cost, learn about our onboarding process, and schedule a live demo with our team.
Need help customizing scans? Contact us via email contact@cybedefend.com.

